The Time for Adoption is Now
CMMC 2.0 certification is now required for manufacturers bidding on Department of Defense contracts in 2026. Phase 1 implementation began November 10, 2025, which means self-assessments are already appearing in new solicitations across the defense supply chain.
If your manufacturing operation touches DoD work—whether you’re machining components, supplying raw materials, or providing engineering services to a prime contractor—this applies to you. The days of self-attestation without verification are over.
For manufacturers in Central Illinois and across the Midwest, the message is clear: get certified or get left behind when contracts come up for renewal.
Facet Technologies helps manufacturers achieve CMMC certification. We assess your current environment, identify gaps against CMMC requirements, and build a realistic action plan to get you certified on time. Our team has worked with manufacturing operations for over 30 years—we understand shop floor realities, legacy equipment challenges, and the documentation requirements that assessors expect.
What Is CMMC 2.0?
CMMC (Cybersecurity Maturity Model Certification) is the DoD’s verification system that confirms defense contractors meet specific cybersecurity standards before contract award. Unlike previous requirements where contractors simply claimed compliance, CMMC requires either verified self-assessments or third-party certification depending on the sensitivity of information you handle.
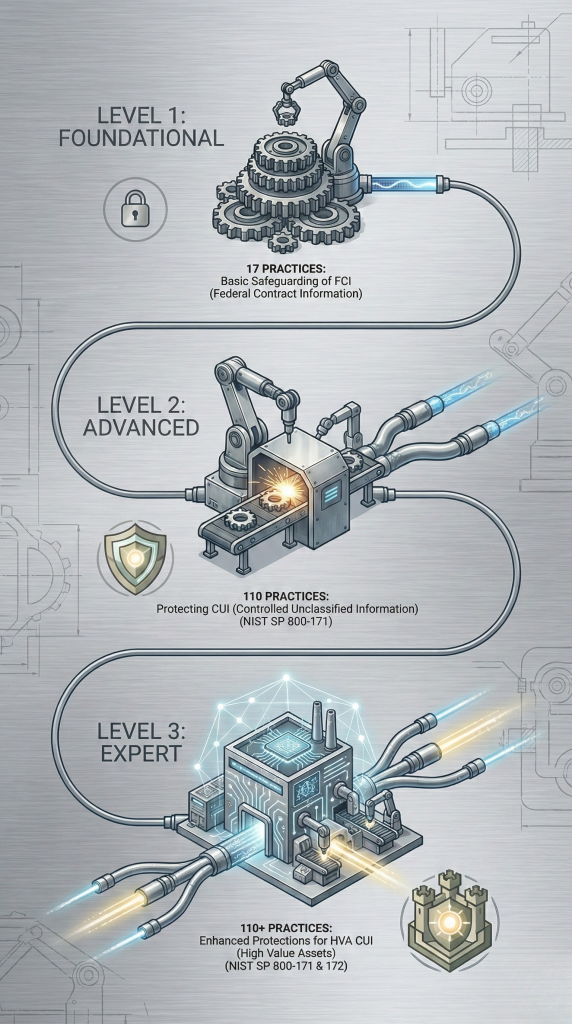
The framework has three levels:
Level 1 (Foundational) applies to manufacturers handling Federal Contract Information (FCI)—things like contract terms, delivery schedules, and pricing. This level requires 15 security practices and allows self-assessment.
Level 2 (Advanced) applies to manufacturers handling Controlled Unclassified Information (CUI)—engineering drawings, specifications, test data, or anything marked as controlled. This level requires full implementation of 110 NIST SP 800-171 controls. Depending on the contract, you may self-assess or need third-party certification from a C3PAO (Certified Third-Party Assessment Organization).
Level 3 (Expert) applies to manufacturers working on the most sensitive defense programs. This level adds 24 additional controls from NIST SP 800-172 and requires government-led assessment by DIBCAC (Defense Industrial Base Cybersecurity Assessment Center).
The Four-Phase Implementation Timeline
The DoD is rolling out CMMC requirements over three years. Here’s what manufacturers need to know:

Phase 1 (November 10, 2025 – November 9, 2026) Level 1 and Level 2 self-assessments appear in new contracts. The DoD can also require third-party C3PAO assessments for high-priority acquisitions during this phase. This is happening now.

Phase 2 (November 10, 2026 – November 9, 2027) Level 2 C3PAO certification becomes mandatory for contracts involving CUI. If you handle controlled technical data, engineering specifications, or defense-related designs, you’ll need third-party verification.

Phase 3 (November 10, 2027 – November 9, 2028) Level 3 DIBCAC assessments expand to more contracts. Manufacturers working on sensitive programs face government-led certification requirements.

Phase 4 (Beginning November 10, 2028) Full implementation across all DoD contracts. No exceptions, no waivers. CMMC compliance becomes a standard condition for any contract involving FCI or CUI.
The phased approach gives manufacturers time to prepare—but waiting until Phase 4 means watching competitors win contracts you could have bid on.
Why Manufacturing Gets Hit Harder
Manufacturers face CMMC challenges that office-based contractors don’t. Your environment is different, and those differences create specific security gaps that assessors will look for.
Legacy Equipment on the Shop Floor CNC machines, PLCs, and industrial control systems often run outdated operating systems that can’t accept modern security patches. That 15-year-old CNC running Windows XP? It’s a compliance problem. You’ll need to isolate these systems or develop compensating controls—and document exactly how you’re protecting them.
Engineering Data Everywhere CAD files, G-code, inspection reports, material certifications—this data flows between engineering workstations, shop floor terminals, supplier portals, and customer systems. Every transfer point is a potential vulnerability. CMMC requires you to know where CUI lives and prove you’re protecting it at every step.
Supplier and Subcontractor Connections Manufacturing supply chains are interconnected. If you receive specifications from a prime contractor or share inspection data with a customer portal, those connections need security controls. Your compliance depends partly on your suppliers’ compliance—and primes are already asking subcontractors to prove CMMC readiness.
Remote Access and Distributed Operations Field service technicians, remote engineers, work-from-home arrangements—each creates access points that need protection. Multi-factor authentication, encrypted connections, and access logging aren’t optional anymore.
The Real Cost of Non-Compliance
Manufacturers who miss CMMC deadlines face concrete consequences:
Lost Contract Eligibility Starting now, contracting officers can exclude non-compliant manufacturers from bidding. By 2028, they must. If you can’t show CMMC certification at the required level, your bid gets rejected—regardless of price, quality, or past performance.
Supply Chain Exclusion Prime contractors face their own CMMC requirements, which include verifying subcontractor compliance. Primes are already auditing their supply chains and dropping suppliers who can’t demonstrate readiness. Even if you don’t bid directly on DoD contracts, your customers might.
False Claims Act Exposure The DoD has increased enforcement against contractors who claim compliance without actually meeting requirements. Recent settlements have reached into the millions. Self-attesting to controls you haven’t implemented creates legal liability.
Cyber Insurance Complications Insurers are tightening requirements for manufacturers in regulated industries. Non-compliance with CMMC—especially after a breach—can affect coverage and premiums.
What CMMC Certification Actually Requires
Meeting CMMC isn’t about checking boxes on a form. Here’s what the process involves:
For Level 1 (15 Practices) You must implement and document 15 security practices from FAR 52.204-21. These cover access control, identification, media protection, physical protection, system protection, and communications protection. Self-assessment results go into SPRS (Supplier Performance Risk System), where contracting officers can verify your status.
All 15 practices must be fully implemented. Unlike previous requirements, you cannot submit a Plan of Action and Milestones (POA&M) for Level 1—everything must be complete.
For Level 2 (110 Controls) You must implement all 110 security requirements from NIST SP 800-171 Revision 2. These controls span 14 families: access control, awareness and training, audit and accountability, configuration management, identification and authentication, incident response, maintenance, media protection, personnel security, physical protection, risk assessment, security assessment, system and communications protection, and system and information integrity.
You need a System Security Plan (SSP) documenting how each control is implemented in your environment. For self-assessment, you calculate a score (maximum 110) and enter it in SPRS. For third-party assessment, a C3PAO auditor verifies your implementation.
Level 2 allows conditional certification with a POA&M, but you must score at least 80% and close all open items within 180 days.
For Level 3 (134 Controls) Level 3 adds 24 controls from NIST SP 800-172 on top of the 110 Level 2 controls. Assessment is conducted by DIBCAC, not a commercial assessor. This level applies to manufacturers working on programs involving national security.
The 6-12 Month Path to Certification
Most manufacturers need 6 to 12 months to reach Level 2 compliance. Here’s what that timeline looks like:
Months 1-2: Assessment and Gap Analysis Identify which CMMC level applies to your contracts. Inventory your systems and data flows. Document where FCI and CUI exist in your environment. Compare current practices against required controls. This phase reveals the gap between where you are and where you need to be.
Months 2-4: Remediation Planning Prioritize gaps based on risk and effort. Some controls require technology changes (new firewalls, endpoint protection, backup systems). Others require policy and procedure updates. Some require both. Build a realistic timeline and budget.
Months 4-8: Implementation Deploy security technologies. Write and approve policies. Configure systems to meet control requirements. This is where most of the work happens—and where manufacturers often underestimate the effort involved.
Months 8-10: Documentation and Testing Complete your System Security Plan. Document how each control is implemented. Test controls to verify they work as intended. Collect evidence that assessors will need.
Months 10-12: Assessment For self-assessment, calculate your score and submit to SPRS. For C3PAO assessment, schedule your audit (book early—assessor availability is limited), conduct the assessment, and address any findings.
Manufacturers with existing security programs and documentation can move faster. Those starting from scratch—or with significant gaps—may need the full 12 months or more.
Facet Technologies: Manufacturing Cybersecurity Experience
Facet Technologies has served Central Illinois businesses for over 30 years, including manufacturers across the region who supply components, materials, and services to defense primes.
We understand manufacturing environments because we’ve worked in them. Our team knows that a machine shop floor operates differently than a corporate office. We’ve helped manufacturers address the specific challenges that come with legacy equipment, distributed data, and supply chain connections.
Our president, Brian Ford, brings quality assurance experience from food manufacturing—an industry where documentation, process control, and regulatory compliance are built into daily operations. That background shapes how we approach CMMC: not as a one-time certification project, but as an ongoing quality system that protects your business.
What We Bring to CMMC Compliance:
We conduct gap assessments that account for manufacturing realities. We don’t just compare your policies to a checklist—we look at how data actually moves through your operation, where your vulnerabilities exist, and what it will take to close them.
We build implementation plans that fit manufacturing budgets and timelines. We know you can’t shut down production to install security controls. We sequence work to minimize disruption while meeting certification deadlines.
We handle the technical implementation. Firewalls, endpoint protection, backup systems, access controls, monitoring—we deploy and manage the security stack manufacturers need for CMMC compliance.
We prepare documentation that passes assessment. SSPs, policies, procedures, evidence packages—we help you build the paper trail that assessors require.
We provide ongoing monitoring and support. CMMC isn’t a one-time event. Certification requires annual affirmation and reassessment every three years. We keep your systems compliant between assessments.
Our approach:
- Assess your current state and identify your required CMMC level
- Map your data flows and document where FCI/CUI exists
- Identify gaps between current practices and required controls
- Build a prioritized remediation plan within your budget
- Implement security controls with minimal production disruption
- Prepare documentation and evidence for assessment
- Support you through self-assessment or C3PAO audit
- Maintain compliance with ongoing monitoring and quarterly reviews
Frequently Asked Questions
Does CMMC apply to my manufacturing business?
CMMC applies if you bid on DoD contracts directly, subcontract to a prime contractor with DoD work, or handle Federal Contract Information or Controlled Unclassified Information as part of defense work. If you’re unsure, look at your current contracts for DFARS clauses 252.204-7012, 252.204-7019, 252.204-7020, or 252.204-7021—these indicate CMMC requirements apply.
What’s the difference between FCI and CUI?
Federal Contract Information (FCI) includes information generated or provided under a government contract that isn’t intended for public release—contract terms, pricing, delivery schedules, and similar administrative data. Controlled Unclassified Information (CUI) is more sensitive: technical data, engineering drawings, specifications, test results, or anything marked with CUI designations. FCI requires Level 1; CUI requires Level 2 or higher.
Can I self-assess for Level 2?
It depends on the contract. Some Level 2 contracts allow self-assessment; others require third-party C3PAO certification. The solicitation will specify which applies. Starting in Phase 2 (November 2026), C3PAO certification becomes the standard for most CUI-handling contracts.
What if I can’t implement all 110 controls by my deadline?
Level 2 allows conditional certification with a Plan of Action and Milestones (POA&M), but you must score at least 80% (88 of 110 controls fully implemented) and complete all remaining items within 180 days. Level 1 does not allow POA&Ms—all 15 practices must be complete.
How much does CMMC compliance cost?
Costs vary based on your current security posture, the size of your environment, and your required level. Gap assessment typically runs $5,000-$15,000, again, depending on the size and complexity of your environment. Remediation and implementation can range from $20,000 for small manufacturers with good existing practices to $100,000+ for larger operations with significant gaps. C3PAO assessment fees typically run $15,000-$50,000 depending on scope. We provide detailed cost estimates after our compliance assessment.
How long does certification last?
CMMC certification is valid for three years, but you must affirm compliance annually in SPRS. Any material changes to your environment require reassessment. Continuous compliance—not just point-in-time certification—is the expectation.
What happens to my legacy manufacturing equipment?
Legacy systems that can’t meet modern security requirements need isolation or compensating controls. This might mean network segmentation, dedicated air-gapped systems, or enhanced monitoring. Your SSP must document these situations and explain how you’re protecting CUI despite technical limitations. We help manufacturers develop compliant approaches for legacy equipment.
Do my suppliers need to be CMMC certified?
This depends on your situation. If your suppliers handle FCI or CUI on your behalf, they need appropriate CMMC certification. Prime contractors are responsible for verifying subcontractor compliance. This requirement flows down the entire supply chain.
Get Started Before Your Competitors Do
Manufacturers who achieve CMMC certification early gain advantages beyond contract eligibility. They demonstrate security commitment to customers and primes. They avoid the rush as deadlines approach and assessor availability tightens. They build security practices that protect against real threats—not just compliance requirements.
The implementation timeline is here. Phase 1 started November 2025. Contracts are already requiring CMMC compliance. Waiting means watching opportunities pass to competitors who prepared.
Schedule a CMMC readiness assessment with Facet Technologies.
We’ll evaluate your current security posture, identify your required CMMC level, map your path to certification, and give you a realistic timeline and budget. No obligation, no pressure—just straight answers about where you stand and what it takes to get certified.
Fill out the contact form below to get started.
Brian is the President of Facet Technologies, Inc. Since 1989, he has helped business owners make smart, profit-driven technology moves. He has grown Facet to support hundreds of companies through managed services, IT support, cybersecurity, and compliance. His career experience in the agriculture and manufacturing industries gives him a unique understanding of their technology needs. He writes about IT and cybersecurity from a growth-focused business owner's standpoint.
